When a company, school, or government decides to turn to blockchain to help them resolve a challenge they’re facing, it’s important for them to identify a few issues as part of their blockchain implementation process. See, it’s not enough to decide that you want to use blockchain as part of your business processes, there are more complexities to analyze and decisions to make. For example, who will be able to access the blockchain and the data that lives on it? To decide this and you should be familiar with the types of blockchain.
Permissioned vs. Permissionless Blockchains
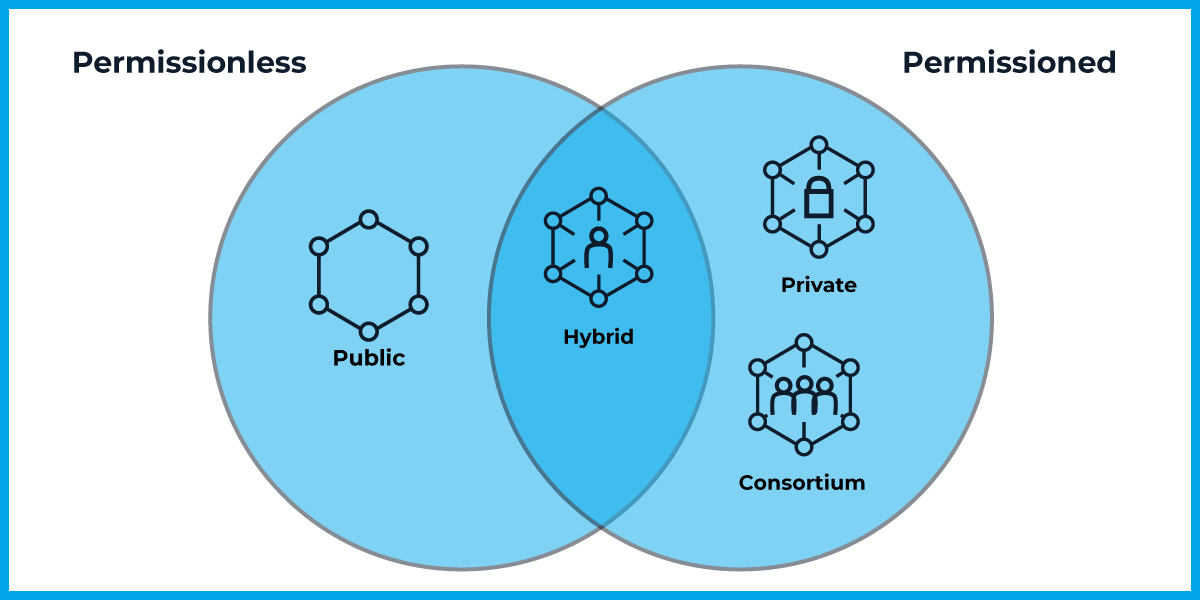
Before we address the four specific types of blockchains, it’s important to understand that there are two categories of blockchains. Every blockchain is characterized as either permissioned or permissionless.
When we talk about a permissioned blockchain, we’re referring to a network which restricts access to certain “nodes”—who are essentially network users and devices—and may limit the nodes’ network rights. The identities of the users are also known to other users on that permissioned blockchain.
Permissioned blockchains tend to be more efficient than their permissionless counterparts. This is because the former has limited access, so there are fewer nodes on the blockchain, and less processing time per transaction.
On the other hand, permissionless blockchains allow any user to pseudo-anonymously join the network and have unrestricted rights on the network.
Permissionless networks tend to be more secure than permissioned networks because there are many more nodes to validate transactions, so it would be more difficult for bad actors to infiltrate the network.
There is technically an overlap in this Venn diagram, but we’ll cover this shortly.
The 4 Types of Blockchain
Now that we understand the differences between the permissioned and permissionless models of blockchain, we can now take a look at the specific types of blockchain:
Since public blockchains are permissionless, anyone can join, and they are completely decentralized. There are still rules, though, the governing principle of public blockchains is known as its consensus algorithm.
At the time of this writing, public blockchains are primarily used for cryptocurrency: the most popular being Bitcoin and Ethereum. On public blockchains, the nodes mine for cryptocurrency—creating blocks for transactions and solving cryptographic equations.
1. Public
Permissioned or permissionless? Permissionless
Since public blockchains are permissionless, anyone can join, and they are completely decentralized. There are still rules, though, the governing principle of public blockchains is known as its consensus algorithm.
At the time of this writing, public blockchains are primarily used for cryptocurrency: the most popular being Bitcoin and Ethereum. On public blockchains, the nodes mine for cryptocurrency—creating blocks for transactions and solving cryptographic equations.
2. Private
Permissioned or permissionless? Permissioned
In a private blockchain, sometimes known as managed blockchains, a single organization controls who can be a node as a central authority. Because of this, private blockchains are only partially decentralized. For data confidentiality, higher levels of privacy are needed; private blockchains provide the stability necessary. Depending on the specific use case, the private blockchain ensures trust and confidence between participants.
Private blockchains are great for business-to-business virtual currency exchange using a network like Ripple or Hyperledger.

3. Consortium
Permissioned or permissionless? Permissioned
The consortium model is similar to the private blockchain model in that it’s permissioned. However, unlike private blockchains, which see one specific organization as the single authority, consortium blockchains have a group of organizations acting as a group of governors. Because of this, consortium blockchains are considerably more decentralized than private blockchains. The downside to this decentralization is that the model requires cooperation between organizations and the logistical challenges that come with it.
A consortium blockchain is ideal for business when all participants need to be permissioned and have a shared responsibility for the blockchain.
4. Hybrid
Permissioned or permissionless? Both
Finally, there’s the hybrid type. Hybrid blockchains seek to strike a balance between the control private blockchains offer and the oversight of public blockchains. The hybrid model allows organizations to establish a private, permissioned model alongside the public, permissionless system. This enables the organization to administer who can access data, but it cannot change the transactions.
Once a user is admitted into the network, he or she will have complete access to the network. In most cases, the user is anonymous, but if he or she takes part in a transaction, then the other user will know who he or she is working with.
Which is Right for You?
Knowing who needs to access the blockchain network, the data that lives on it, and the four types of blockchain will help you make informed decisions and get your project on the right track. So, whether you’re a manufacturer seeking out ways to make your processes more efficient, a government working on supply chain issues, or a school integrating badges and certifications into your curricula, the SIMBA Chain team is here to help you achieve the goals you set for your blockchain project. Interested in learning more? Contact us!